Have you ever been in a situation where you needed to perform remote administration on a Windows Server, and the RDP port 3389 is blocked on a firewall? Did you know you can tunnel RDP over SSH with PuTTY? This particularly comes in handy when there is no VPN available to the remote network… Here is how to set up a RDP SSH tunnel with PuTTY.
Proxy connections with SSH
SSH can proxy connections both forward and backwards. It creates a secure connection between a local computer and a remote machine through which services can be relayed. Because the connection is encrypted, SSH tunneling is useful for transmitting information that uses an unencrypted protocol, such as IMAP, VNC, or IRC. And RDP 🙂
SSH can proxy connections both forward and backwards, by opening a port on either the local machine running the SSH client, or the remote SSH server. If you have privileges to do so of course.
For example, if you want to connect to a remote host on RDP port 3389, but you don’t have direct access to reach that machine because of firewall or network restrictions, the SSH client can listen on a local port and pretend that it is the remote machine. All connections to that port will be sent through the SSH server to the remote host.
Tunnel Remote Desktop Protocol (#RDP) through #ssh with PuTTYCLICK TO TWEET
Reconfigure PuTTY for Remote Desktop Protocol (RDP) tunneling through ssh
To tunnel Remote Desktop Protocol over ssh using PuTTY, all you need is an account on the premises. For example a firewall or Linux server with ssh access, and PuTTY on your Windows desktop. PuTTY is a nifty ssh client for Windows that you can download here.
Once you are connected to your remote network with ssh/PuTTY, you need to reconfigure the connection to support SSH-tunneling. In the PuTTY Reconfiguration screen, go to Connection → SSH → Tunnels. This is where we can set up an SSH tunnel for Remote Desktop.
Under Source port, add your local IP address and port. Because the RDP 6+ client in Windows has issues with the loopback to TCP Port 3390, you need to use a different port. I use TCP port 3388 on IP address 127.0.0.2, and my remote internal IP address and RDP port 3389 as Destination (192.168.48.211:3389). See the image:
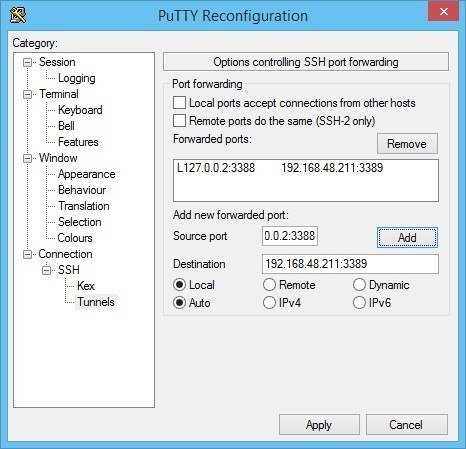
After clicking Apply, the SSH-tunnel for remote desktop is active, and you can connect the Remote Desktop Connection to 127.0.0.2:3388:
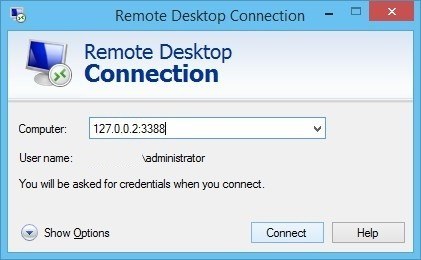
For Windows, PuTTY is the de-facto standard SSH client.
How to tunnel Windows Remote Desktop through ssh on Linux
On a side note, when you are in a situation where you are on a Linux work station and need to tunnel RDP through ssh in Linux, you can use the following ssh port forwarding, or tunnel (assuming you have an on-premise Linux server to SSH into to set up the port forward):
ssh port forwarding / tunnel set-up for RDP
ssh -L 13389:[Windows Server RDP address]:3389 [address ssh server] -l [ssh username] -NNow you can connect your RDP client to 127.0.0.1:13389 as if it were the remote server.